Data Destruction Solutions: A Crucial Element in Your Cyber Security Approach
Data Destruction Solutions: A Crucial Element in Your Cyber Security Approach
Blog Article
The Important Nature of Information Damage in Upholding Computer System Safety Providers and Protecting Versus Unauthorized Accessibility
In a period where data violations and identity theft are progressively prevalent, the importance of effective information destruction can not be overstated. Organizations should recognize that the failing to effectively dispose of delicate info postures not only legal and financial dangers but additionally a possible erosion of client count on. Numerous methods, from data wiping to physical devastation, function as vital safeguards versus unapproved accessibility. Nevertheless, comprehending the ramifications of data damage methods and compliance with laws raises crucial questions about the adequacy of present approaches and their long-term stability despite advancing risks.
Significance of Information Devastation
In a progressively digital world, the value of information damage can not be overstated. As companies generate vast quantities of delicate info, the potential repercussions of falling short to properly manage and dispose of that information become significantly serious. Information violations, identity theft, and corporate reconnaissance position significant threats, highlighting the requirement of efficient data destruction methods.
In addition, as modern technology advances, so as well do the methods through which harmful actors look for to exploit delicate information. Organizations must remain alert and positive in their information devastation strategies to guard against these progressing dangers. By prioritizing information devastation, firms not only secure their assets however likewise foster count on amongst customers and stakeholders, showing a commitment to accountable information management and security techniques.
Techniques of Effective Information Destruction
To ensure the irreparable and full devastation of sensitive data, companies can use a variety of efficient techniques tailored to their particular requirements. One of the most typical approaches is information cleaning, which involves using specialized software program to overwrite existing data numerous times, making healing essentially impossible. This is especially valuable for solid-state drives and hard drives, where traditional deletion methods are insufficient.
An additional reliable technique is degaussing, which uses strong magnetic fields to disrupt the magnetic domains on storage media, providing the information irretrievable. This technique is especially suited for magnetic storage gadgets, such as tape drives and hard drives.
Physical damage is likewise a feasible alternative, involving the shredding, crushing, or incineration of storage space devices. This method guarantees that data can not be recuperated, making it perfect for organizations taking care of extremely delicate information.
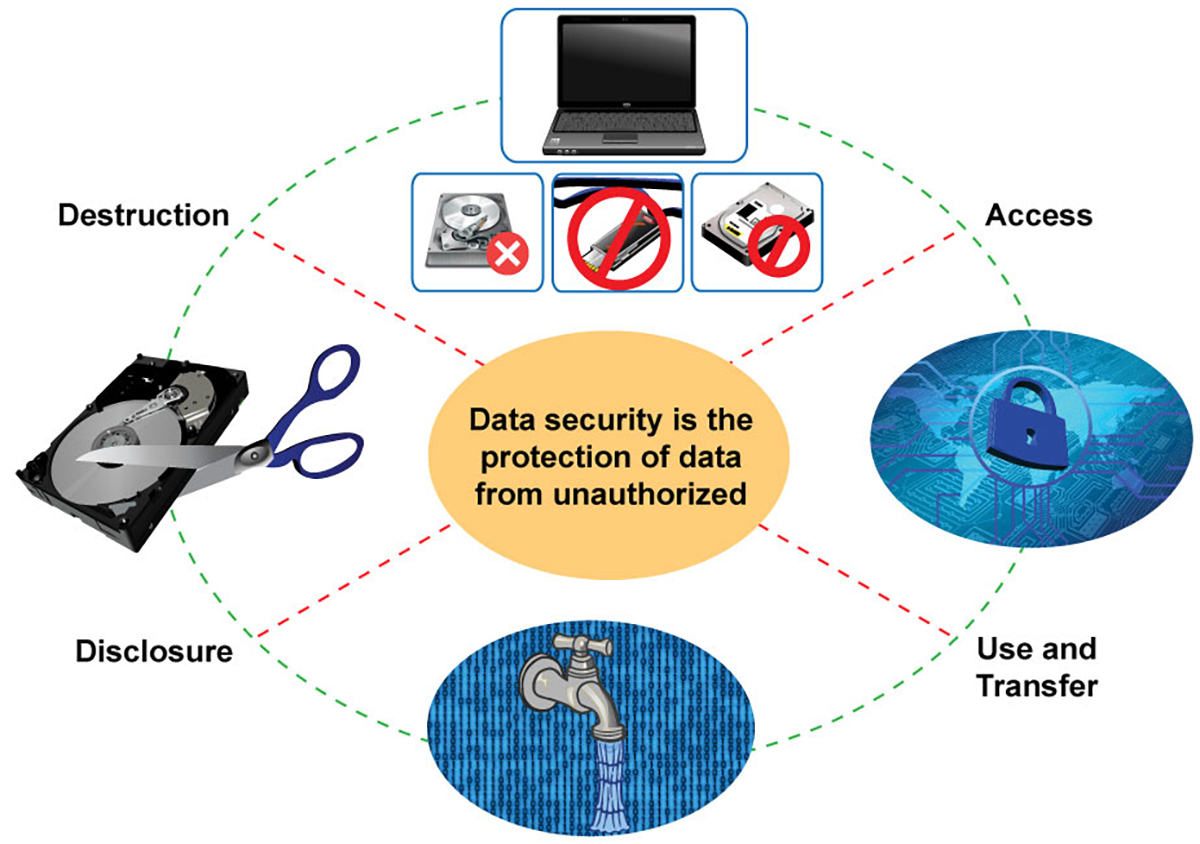
Compliance With Data Defense Laws
Organizations must not just concentrate on reliable data devastation approaches however additionally ensure compliance with data defense guidelines that control exactly how delicate details is managed and disposed of. Complying with these regulations is essential for protecting personal data and keeping consumer trust. Regulations such as the General Data Protection Regulation (GDPR) in the European Union and the Medical Insurance Mobility and Responsibility Act (HIPAA) in the United States enforce strict guidelines on data monitoring, that include needs for the safe and secure disposal of delicate info.
To accomplish compliance, organizations need to implement thorough information destruction plans that straighten with these legal structures. This consists of recognizing information that calls for destruction, establishing protocols for safe methodsâEUR" such as shredding physical media or utilizing software that fulfills sector criteria for data wipingâEUR" and preserving comprehensive documents of devastation activities. Routine audits needs to be conducted to make sure adherence to these policies and to recognize any potential areas for improvement.
Failing to follow information protection regulations can result in considerable lawful implications, including hefty penalties and damage to a company's track record. Integrating conformity right into data destruction methods is not just a legal responsibility yet additionally an essential part of a robust info security technique.
Effects of Poor Information Handling
Poor data handling can result in serious repercussions that expand past instant operational problems. Organizations might face considerable economic losses as a result of data violations, which frequently result in pricey removal initiatives, lawful continue reading this costs, and regulative penalties. These economic ramifications can stress sources and hinder growth, inevitably affecting a company's lower line.
In addition, inadequate data handling can severely harm a company's online reputation. Clients, stakeholders, and partners may shed trust fund in an entity that falls short to protect delicate info, resulting in decreased client commitment and possible loss of service possibilities. This disintegration of trust fund can take years to rebuild, if it can be restored in all.
Furthermore, companies could encounter lawful implications arising from non-compliance with information protection laws. Such offenses might result in charges and investigations, worsening the economic burden and additional tainting the organization's photo.
In the realm of cybersecurity, insufficient information monitoring practices can develop vulnerabilities that make systems extra at risk to unapproved access and cyberattacks. Ultimately, these effects highlight the essential value of executing durable information taking care of procedures to safeguard sensitive information and maintain organizational stability.
Finest Practices for Secure Data Disposal


To start with, data need to be identified according to its level of sensitivity. click this link Delicate info calls for much more strenuous disposal approaches, such as shredding physical files and using innovative software program for electronic data wiping. Employing certified data damage services makes certain conformity with sector guidelines and criteria.
Second of all, organizations should apply a data disposal policy that mandates normal audits. This policy must lay out the treatments for data retention and destruction, making sure that outdated information is dealt with immediately and firmly. Educating staff members on these procedures is crucial to promoting a culture of safety understanding.
Lastly, maintaining detailed records of disposed data enhances accountability and provides a clear audit route. This documents needs to consist of the kind of information damaged, the approach used, and the day of disposal.
Verdict
Adopting durable methods such as information wiping, degaussing, and physical destruction, together with compliance with regulations like GDPR and HIPAA, is crucial for protecting sensitive info. Overlooking correct information disposal methods can lead to extreme effects, consisting of data violations and legal consequences.
In an age where data breaches and identity theft are significantly prevalent, the value of efficient information damage can not be overstated. data destruction. Data violations, identification theft, and company espionage position significant dangers, highlighting the requirement of efficient data destruction methods
Compliance with guidelines such as GDPR and HIPAA requireds that companies implement rigid information protection actions, including the protected devastation of information at the end of its lifecycle.
By prioritizing data devastation, business not only safeguard their assets yet also foster depend on among stakeholders and customers, showing a dedication to liable data administration and safety and security techniques.
Organizations must not just focus on reliable data devastation methods yet also guarantee compliance with information protection policies that control how sensitive details is dealt with and disposed of.
Report this page